Bank Hackers and Smartphones: Managing Points of Exposure
The August 27, 2016, print edition of the Wall Street Journal ran a front-page article by Robin Sidel called Bank Hackers Target Smartphones [view the online article here]. The author provided a general description of how cyber thieves are deploying malware that targets smartphones and is designed to capture the victim’s online banking credentials. Some of these techniques even involve overlay screens allowing them to harvest more confidential data through additional questions.
Knowing that this is not just a possibility but a reality should heighten our senses and force treasury groups to reexamine their security framework. Sidel indicated that this trend is ‘alarming the Federal Bureau of Investigation and U.S. banking regulators’.
While each person will want to be careful with their personal online banking access and device hygiene, every treasury professional will want to review some of their corporate banking controls.
Understanding and mitigating the risks at the various points of exposure and access is vital. When we think about how we manage devices, authentication and overall access, particularly for transaction initiation and approval, we must ask, “What are other corporations doing? How are they restricting access? How are they controlling devices – particularly mobile/phone devices? How would you answer these questions?”
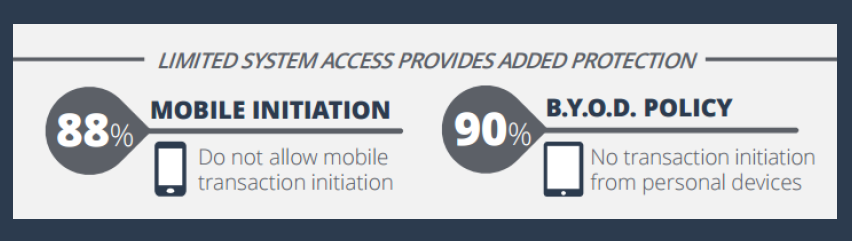
- BYOD. Do you allow a Bring Your Own Device (BYOD) and allow transaction initiation (such as wire transfers)? 90% of the respondents DON’T allow this. [download infographic]
- MOBILE. Do you allow mobile devices to initiate transactions (such as wire transfers)? 88% of the respondents DON’T allow this. [download report]
For the 12% of firms that allow mobile devices to be used to initiate transactions, what security do you require on those devices? And, what extra steps, controls, or out of band (OOB) authentication do you require? For the 88% that don’t, how systematic are you with regard to your controls on the devices and access methods used to generate or transmit payments?
Having system-enforced segregation of duties that are typical in corporations provides a better level of security than an individual accessing their personal banking system. Nonetheless, the access to vastly larger amounts of money from corporate accounts is surely in the sights of cyber criminals. The payoff is so large it is worth the extra effort to defeat the level of controls that many organizations currently deem adequate. Let’s agree that it is worth having another look at your security now.



