Treasury Fraud & Controls, Part 3:
Mounting an Effective Defense
We’ve seen plenty of bad news about fraud. Scams are coming faster, more of them are succeeding, and companies’ losses are mounting. Many organizations are under-protected and insufficiently prepared. The data and analysis showing these facts are well-documented. Fearmongering, however, isn’t our goal. Equipping is. So with multiple years of data in the vault from our Treasury Fraud & Controls Surveys, we set out to find, analyze, and learn from successes against fraud.
We are excited to share the results, as the data points to certain practices appearing to have a noticeable – sometimes even dramatic – impact on actual or realized losses (not just attempts). Caveat: It’s important to note that two data points linked together do not prove causation. That said, we have done our best to dig into the data, weed out red herrings, and present the most interesting and defensible correlations.
Correlations
Our analysis showed three specific activities and/or security measures that correlated most strongly to lower levels of realized loss to fraud:
- Principle of Least Privilege: Corporate respondents employing the principle of least privilege – giving each user of their systems only the permissions strictly necessary for their role – experienced 55% fewer losses or issues with ransomware.
- Payment Fraud Interdiction: The use of payment fraud solution suites specifically with interdiction capability corresponded to 75% fewer BEC/imposter/CEO fraud losses.
- Training: Perhaps the most impressive statistics go to employee training on payment fraud, controls, and cyberfraud. Companies that neglected to train saw significantly more losses to multiple different types of fraud. The factors (in terms of how much more fraud was experienced by companies who did not train) are listed below:
- 5x Payment Diversion Fraud
- 2x ACH Fraud
- 5x System Level Fraud (system takeover)
- 4x Business Email Compromise
- 4x Bank Mandate Fraud
- 5x Cyberfraud/Malware
- 5x Ransomware
As established in the previous posts on this topic, ransomware and BEC (Business Email Compromise) fraud are two of the most concerning currently, with average losses to ransomware rising steeply in 2019 and with BEC landing a position as the most common type of fraud attempted and the most common type to find success. This makes it especially exciting to find weapons in our arsenal correlating to dramatically fewer losses to those two in particular.
Obviously, however, the triad of least privilege, interdiction enabled fraud solutions, and training are not an all-encompassing cyber security framework, much as the correlations above may provide a compelling reason to include them in that framework. The heightened threat levels of fraud merit a fresh and thorough examination of your security at large.
Protecting the Payment Processes in Your Organization
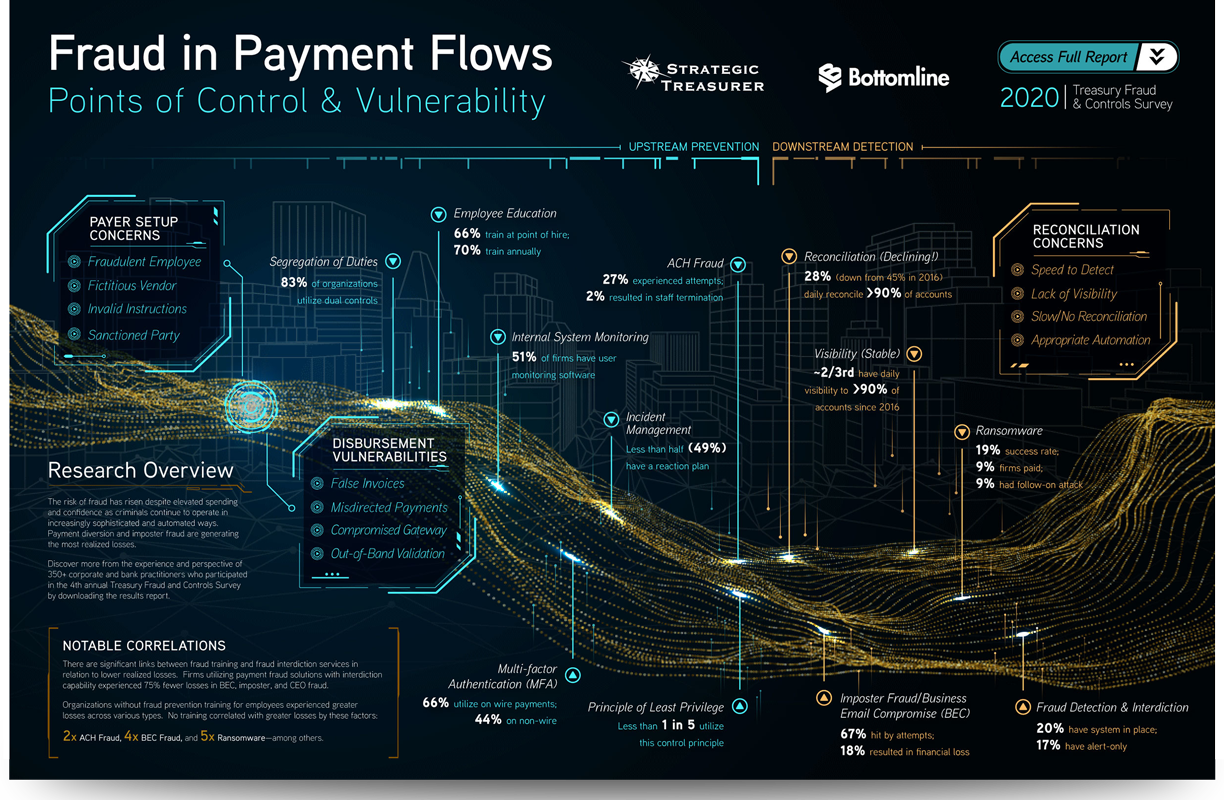
As illustrated in this infographic (click through to view the full image), payment processes run through an organization like a river, with many points of control and vulnerability. At each point of vulnerability, fraud can flow into the river like a pollutant and eventually cause payments, data, or resources to be diverted off their proper paths. As treasurers, this river is ours to steward, and for many organizations, a fresh look at its protection is overdue.
In order to ensure the protection of the payment flow, it is necessary to take an end-to-end view of it. We must find and note every access point and every vulnerability, and each one should have countermeasures put in place.
These countermeasures and protections come in two basic packages: technology and people. Both require “updates” to remain secure, and without those updates, they can become vulnerabilities themselves.
As noted in a previous post in this series, treasury is spending more on securing their technology, and this heightened spend correlates to a heightened feeling of confidence regarding fraud resistance. This confidence seems poorly placed in light of the constant uptick of fraud, but the instinct to invest in security on the technological side is commendable.
Treasury must, in any case, be careful to resist the panicked urge to throw money at the problem without carefully considering what solutions will provide the most effective defense for their unique payment flows. Additionally, organizations should consider technology, sometimes newer technology, that can help address emerging and zero-day threats. Whatever you decide on, you might want to consider implementing a payment fraud solution with interdiction, judging from the correlations above.
We have seen with cyber criminals, however, that the technology is only as effective as the one leveraging it, and the same is true on the defensive side. The human element is far too often ignored, leaving gaping vulnerabilities that hackers are becoming increasingly adept at exploiting. People need updates just as much as their software does. We need “patches” in our knowledge when new types of cybercrime appear. As seen in the correlations, the effects of employee training can make or break the success of some of the most dangerous and costly fraud attempts.
If we attend vigilantly to both the digital and the personnel sides of security and implement the elements of fraud prevention that correlate strongly to decreased losses, most vulnerabilities in the payment flow can be mitigated. Perhaps we can finally make the criminals’ lives as hard as they make ours.
So even with fraud on the rise, there is good news. It isn’t the kind of good news that should set us at ease, but it’s the kind that should give us hope and spur us on to build out our defenses, knowing that there are ways we can fight fraud effectively.
Access to the 2020 Treasury Fraud & Controls Survey Results Report here.